A Network of 328,000 Domains Uncovered in Indonesia
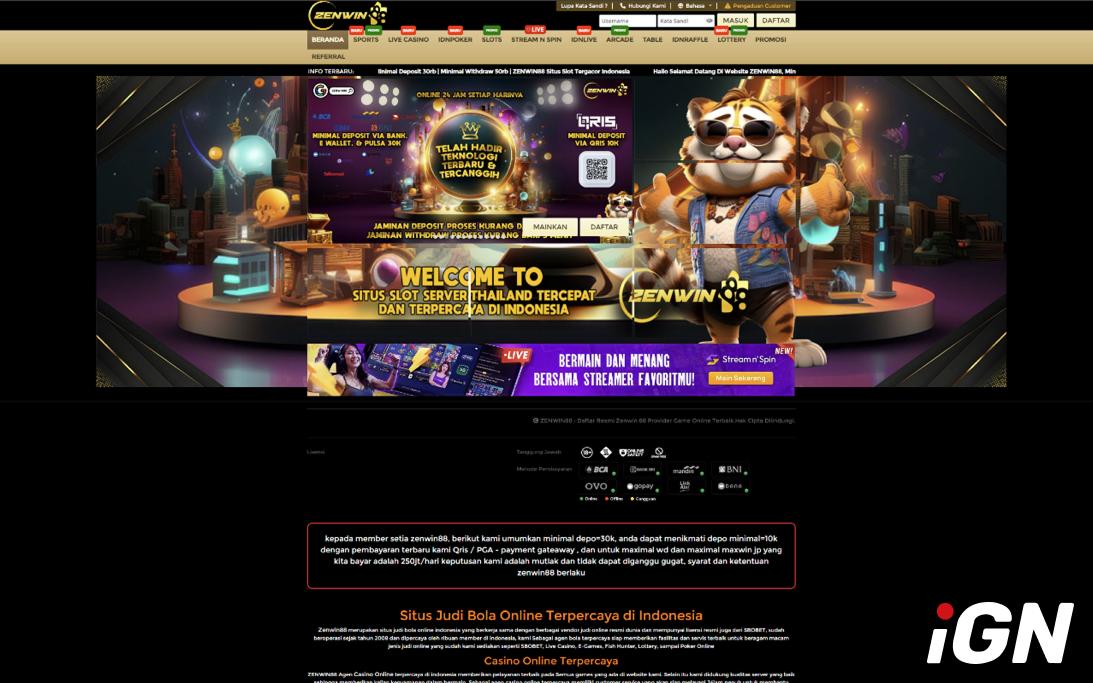
The Malanta platform has discovered a network of 328,000 domains with illegal gambling websites, which are reportedly used for C2 servers and the anonymization of cybercriminal activity.
The network includes 236,000 purchased domains, 90,000 hacked websites, and 1,500 compromised subdomains, including sites of government institutions in the US, the EU, and Israel. Investigators also identified 38 GitHub accounts hosting web shells, thousands of malicious Android applications, and 480 fake organizational domains. Some of the domains imitate “Lazada” (85,000), “Envato” (35,000), and “eBay” (1,800). The network has been operating since 2011.
Purpose of the Infrastructure and How It Operates
According to the research, the primary function of this infrastructure is to redirect users to illegal Indonesian online casinos. All forms of gambling are prohibited by law in Indonesia.
Access to the websites is restricted by geolocation. Registration requires a phone number with the +62 country code and details of Indonesian banks and payment services, including BCA, Mandiri, BNI, BRI, CIMB Niaga, as well as e-wallets such as DANA, OVO, Gopay, and LinkAja.
All websites use a single template and the livechatinc.com support service. The domains are mainly hosted via Cloudflare, while the IP addresses are linked to the United States.
Malicious Android Applications
Researchers identified 7,700 domains connected to at least 20 AWS S3 buckets that hosted thousands of APK files with gambling-related names.
After installation, the applications download additional APK files, gain access to device storage, and use push notifications through Firebase Cloud Messaging. The code contains embedded credentials and API keys.
Some of the applications use a shared domain, jp-api.namesvr[.]dev, which likely performs the functions of a C2 server.
Compromised Domains and Subdomains
Compromised Domains
It was established that 90,125 domains were compromised to host links to illegal gambling sites. The content is often disguised as the pages of well-known services.
HTML templates imitate the interfaces of Lazada, eBay, and Envato. More than 108,000 domains are hosted on approximately 600 IP addresses, with each IP serving hundreds of websites.
Compromised Subdomains
At least 1,481 compromised subdomains were identified, hosted on AWS, Azure, and GitHub. Organizations from manufacturing, logistics, healthcare, education, and the public sector were affected.
Some subdomains were used to host fake versions of popular services. In certain cases, subdomains of government organizations were used to proxy traffic via NGINX with HTTPS decryption and forwarding of data to the attackers’ servers.
In several instances, the subdomains inherited cookies from the main website, creating the risk of user session theft.
GitHub and Stolen Data
38 temporary GitHub accounts were used to host malicious templates, web shells, and service files. Activity on these accounts has been recorded since 2022–2023.
In addition, 51,000 stolen credentials linked to this infrastructure and infected devices were found on the dark web.
Assessment of the Infrastructure’s Scale
The head of Malanta, Kobi Ben Naim, estimated that maintaining such an infrastructure costs hundreds of thousands to several million US dollars per year. According to him, the group is likely of Indonesian origin, but no evidence of ties to government structures has been identified.
