North Korean Hackers Breach Canadian iGaming Operator via Fake Zoom Call
An unnamed Canadian online gambling operator has fallen victim to a targeted cyberattack by the BlueNoroff group, a subunit of North Korea’s notorious Lazarus Group.
How the Attack Unfolded
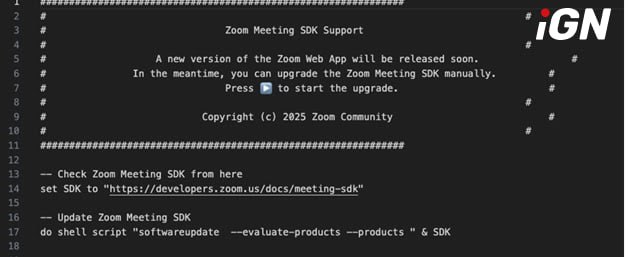
According to a report by Field Effect Analysis, the attackers posed as a trusted contact during a pre-arranged Zoom meeting related to cryptocurrency. They used a fake domain, zoom-tech[.]us, to impersonate the Zoom platform.
Under the pretense of troubleshooting audio issues, they convinced a staff member to run a so-called “audio system update” script. This script was malicious, concealing harmful commands among 10,000 blank lines to evade detection.
Infection Details
- The script redirected the victim to a spoofed website registered on April 14, 2025, with falsified WHOIS data.
- Once executed, it downloaded malware designed to steal credentials, browser profiles, and system data.
- Attackers used
curlandzshcommands, and even replaced system components like the macOS “Wi-Fi Updater.” - Stolen data was exfiltrated via command-and-control (C2) domains such as ajayplamingo[.]com and zmwebsdk[.]com.
What the Malware Targets
BlueNoroff’s malware focused on extracting financially valuable data. Primary targets included:
| Data Type | Description |
|---|---|
| System Information | Device specs and configuration details |
| Browser Data | Particularly interested in crypto wallets, especially within the Brave browser |
| Telegram Accounts | Messages and account access were compromised |
| Passwords | Local user-stored credentials |
| Keychain Files | Extracted data from macOS secure storage |
Evasion and Persistence Techniques
BlueNoroff employed advanced tactics to maintain stealth and persistence:
- Automatic deletion of files post-execution
- Use of temporary directories to minimize traces
- Installation via LaunchDaemon to ensure auto-start with elevated privileges
- Injection into system processes using administrative permissions
BlueNoroff’s Objectives
As a financially motivated arm of the infamous Lazarus Group, BlueNoroff specializes in profit-driven cyberattacks.
Previous targets include:
- The Bybit cryptocurrency exchange
- The blockchain game Axie Infinity
Their primary focus is on financial institutions, crypto companies, and regional targets in Canada, South Korea, Japan, and Europe.
Protection Recommendations
Cybersecurity experts advise the following to defend against similar attacks:
- Restrict execution of unverified scripts
- Implement domain-based filtering rules
- Educate staff to identify social engineering tactics
- Monitor Zoom and other communication platforms for unusual activity
Conclusion
The BlueNoroff breach of a Canadian iGaming operator via a fake Zoom call highlights the dangerous blend of social engineering and technical sophistication. This incident underscores the critical need for cybersecurity awareness and vigilant external communication protocols.
